Why some CIOs say it’s time to rethink governmentwide cyber metrics
One of the biggest complaints about the Federal IT Acquisition Reform Act scorecard is how it measures cybersecurity progress.
The challenge is there are too many cyber metrics so a “C” grade on the scorecard doesn’t necessarily translate into progress made against other governmentwide metrics say under the President’s Management Agenda.
Andre Mendes, the chief information officer at the Department of Commerce, was one of several technology leaders who explained to Congressman Gerry Connolly (D-Va.) and the Government Accountability Office why they believe a re-calibration of cyber metrics is important and necessary.
“In an area as sensitive as cybersecurity, everybody is keenly aware of it, and to a certain degree, it hurts your credibility when the score is one thing on one side and other thing in another side. How do you portray that?” Mendes said in an interview after the Sept. 26 FITARA roundtable, which played on Ask the CIO. “The reality is that the metrics are different, and as a result, the scores come out different and they reflect different situations and nuances within the cybersecurity arena. If we could have some degree of standardization across that, I think it will be very beneficial.”
Connolly released the 16th FITARA scorecard last week with agencies earning 3 “As”, 16 “Bs” and 5 “Cs.” Six agencies received a “D” grade under the cyber category. Under the PMA metrics, no agency received a score lower than what equates to a “C” or meeting at least 70% of the cyber metrics.
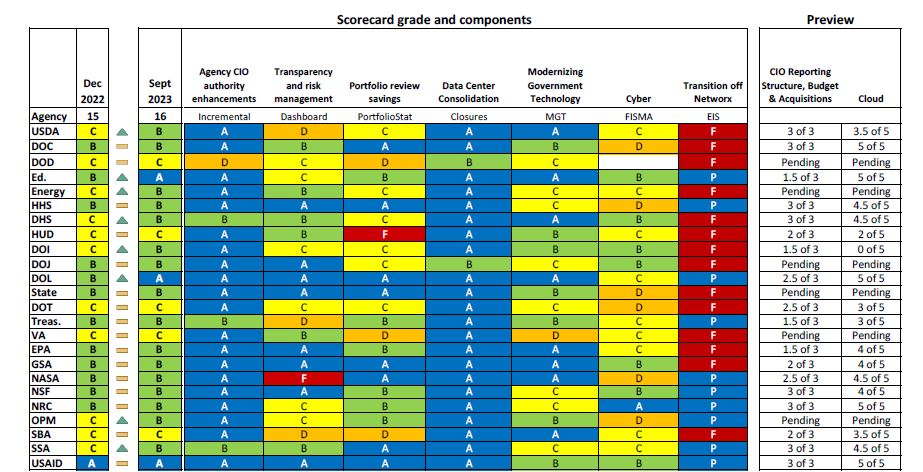
Mendes’ desire for more standardization was a common theme that emerged at the FITARA roundtable as well as previous scorecard hearings.
State Department CIO Kelly Fletcher said the FITARA cyber goals need to continue to evolve to include operational cybersecurity and take a more “holistic approach” across the enterprise.
“I have a lot of cybersecurity scores and some are not public and some are, but even just with the public ones, I’ve got a Performance.gov score, which we are killing it. Then I’ve got my FITARA score and my cybersecurity score is a ‘D.’ I also have my agency priority goal scores, which are cybersecurity related. I think in no way to impugn any of the scores, I think they’re all really valuable. But the problem is when I try to explain to my leadership how are we doing on cybersecurity, frankly, I can pick and choose,” she said. “I think some consistency across these couple of metrics will be very helpful. I think also just to give a plug for the Performance.gov metrics, I really liked that they are grading me on have I done and the things that I need to do that were breaking recently. I get all these cyber directives, a huge amount of time and energy is spent implementing them. I think having that as part of the metric is really valuable.”
Sean Brune, the CIO at the Social Security Administration, echoed Fletcher’s comments, saying the variations in the metrics and reporting requirements makes it too inconsistent to really understand progress. He, too, supported the Performance.gov metrics as a good starting point.
Under the Performance.gov metrics, the Office of Management and Budget measure are derived from the Federal Information Security Management Act (FISMA) metrics and aligned to the National Institute of Standards and Technology’s Cybersecurity Framework around identity, protect, detect, respond and recover.
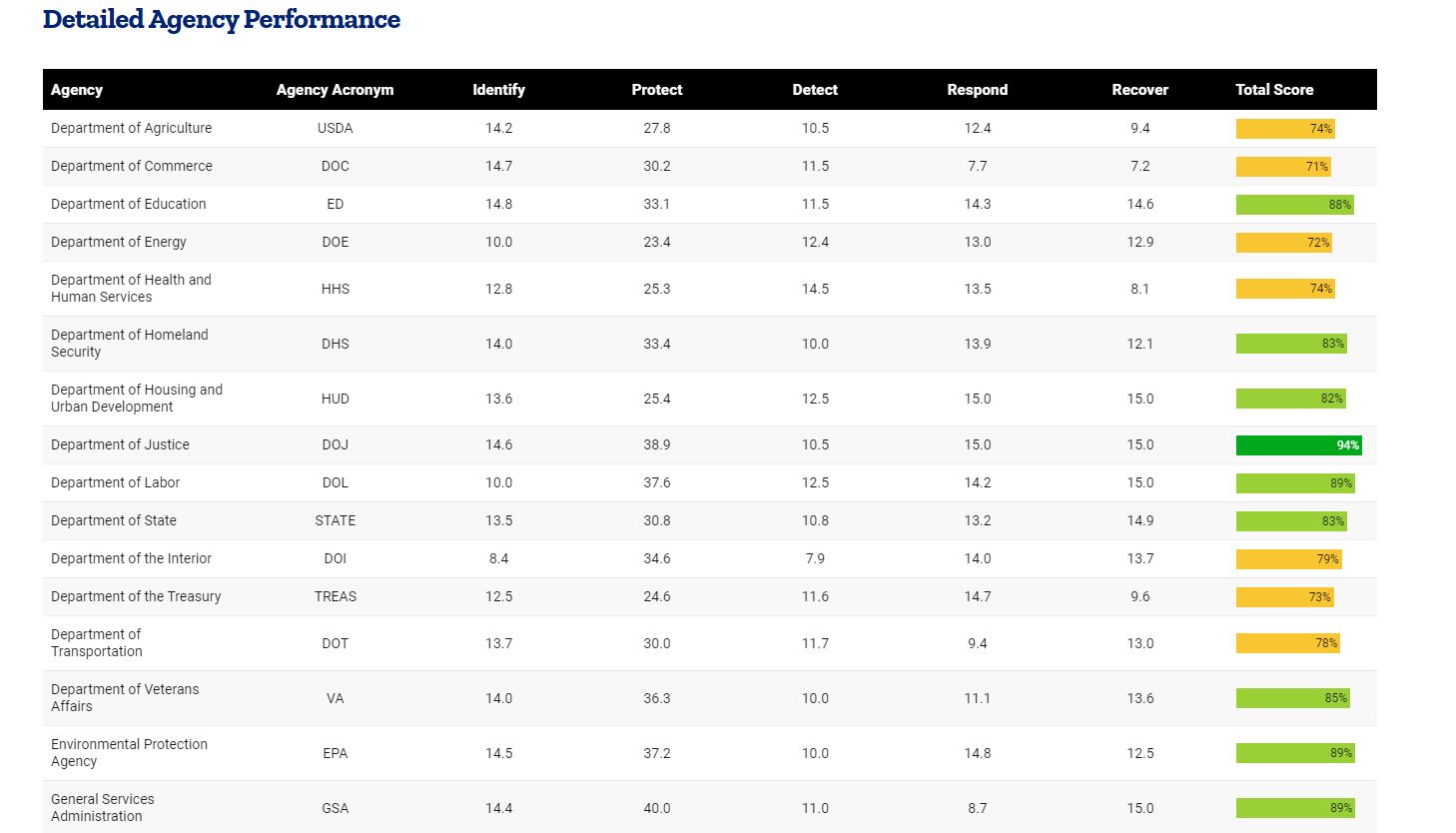
Mendes said the Performance.gov metrics are more predictable and lets agencies target particular areas for improvement, which is “one of the attractive new parts of that equation.”
Connolly said the feedback was helpful and reminded the roundtable participants that the scorecard reflects the focus areas outlined in the FITARA legislation.
“We were vividly aware of the fact that we’re competing scores, and they’re evolving too so I think it’s good feedback for us to try to at least take cognizance of those other measurements,” he said.
Connolly is considering updates to the FITARA scorecard, including adding cloud migration and broadening the CIO authorities category to focus more on budget and procurement.
Mendes said no matter the metrics, Commerce’s progress in improving its cyber posture is real.
He said despite the “D” grade under FITARA, Commerce has been on a clear path to consolidate, virtualize, co-locating and moving to the cloud.
Commerce accelerates move to cloud
Two examples of those efforts are in the financial management and grants management areas. Commerce is consolidating and modernizing those back-office systems using cloud services in the coming weeks.
Mendes said the financial management modernization initiative will consolidate three different systems that have been around for more than 20 years.
“We’re migrating into a software-as-a-service environment. That is one instance for all of the bureaus. That migration will be gradual over three years, but that is basically being done without customizations so that we have the interfaces to other systems. We’re relying on out-of-the-box functionality. We think that’s going to be a major leap forward for us,” he said. “It’s SaaS and it effectively obviates three data centers over a certain period of time. And because the platform is a best practices from both the private sector and the federal environment, the reporting capabilities and the financial agility that you get from knowing exactly where you are at the end of every day is something that we don’t have the luxury yet today.”
He said the new system also will give Commerce a centralized dashboard to better understand how each bureau is doing from a financial perspective. Mendes said that is going to be a major boon for the management of the budget at Commerce.
The migration is going to a private cloud provider and it’s being led by the CFO’s office.
The second system is for grants, which the CIO’s office is leading this migration to the Department of Health and Human Services grants management shared service.
Mendes said Commerce is consolidating about 29 systems.
“We are also not issuing any customizations and we’re going to have one source code that’s going to service everybody. If we have something to contribute from a requirement standpoint, then the requirement is something the Quality Service Management Office (QSMO) agrees to customize or change in their source code. So that is going to benefit all of the federal government,” he said. “The progress we’ve been able to make, even under those very strict requirements, has been great. I’m hoping that in about a week we will start to transition, and if budget permits, within a month or so we will be finished with our major transition.”
Mendes said he expects both migrations to bring significant benefits, including cost avoidance or savings from no longer having to support the legacy systems.
“I think our return on investment will be very fast. So that’s a great thing. Now, most of those savings are cost avoidance and will be gathered at the bureau level,” he said. “We have to continually sell them on the idea that there should be some degree of a reinvestment into modernization so that we can continue moving forward and create, effectively a virtuous cycle of savings and cost avoidance and investment into new stuff so that we accelerate our migrations.”
